Anything useful I find and decide to write down in my geeky wanderings of the web. While some guides make reference to torrents please be aware that I do not conduct or condone illegal downloading, and I do not share the views of any external site I may link to. This site is merely for informational purposes. Any purchases made from clicks on links to products on this page may result in an affiliate commission for me. As an Amazon Associate I earn from qualifying purchases
Featured Post
HOW TO: Install VPN server on Ubuntu when server is behind firewall
The whole point in this post is to run your own VPN service, and allow you to connect remote devices to your home network. To start off yo...
Oct 12, 2017
HOWTO: Notify user joined your Minecraft server (Nukkit or similar) using Notify My Android
So I setup a Minecraft server for my son and his friends, but it is hard to coordinate when they will all get online - so I decided to look into my options for notifications. In the end I went with Notify My Android (NMA). The NMA website provides a complete script for sending notifications via the Raspbian shell. The script can be found at the following location, I used the shell script, but there are other options - this guide focuses on the shell script:
http://www.notifymyandroid.com/dev.jsp
First thing we are going to do is log into our Raspbian system and let's make sure timezone is configured correctly:
sudo dpkg-reconfigure tzdata
Now let's download the notification script from NMA to your Raspberry Pi Minecraft server:
wget http://storage.locked.io/files/nma.sh
We need to do a couple of things with this file, first we need to make a change so that our NMA API key is in the file, using the following command:
sudo nano nma.sh
Edit APIKey= to use your API Key, you can find your own API Key from the NMA site.
Now we have to make the shell script executable:
chmod +x nma.sh
At this point we have a shell script that allows us to send notifications from Raspbian to NMA servers, and then to your Android. The next step is to create a short Perl file to monitor the Nukkit server.log (or any other log file for that matter). This script looks at the entire file, not just the tail, so if you run it against an existing server you are going to get a few notifications when first run. I called my file notify.pl:
sudo nano notify.pl
Enter the following into the notify.pl Perl script:
#Change /location/of/server.log in the following line to the real location of your server.log file
open(my $fd, "<", "/location/of/server.log") or die "Can't open log";
while(1) {
if(eof $fd) {
sleep 1;
$fd->clearerr;
next;
}
my $line = <$fd>;
#Parse the line into variables
my ($date, $time, $loglevel, $user, $operation) = split / /,$line;
chomp($line);
if($line =~ m/joined/) {
system("./nma.sh \"Minecraft\" \"$user Joined\" \"At $time on $date $user $operation.\" 1");
} elsif($line =~ m/left/) {
system("./nma.sh \"Minecraft\" \"$user Left\" \"At $time on $date $user $operation.\" 1");
}
}
Much like the NMA script we have to make our Perl script executable:
chmod +x notify.pl
That's it! Now you are going to have to run this at startup, much like you run your Minecraft server, so edit crontab:
crontab -e
Enter the following at the end of your file:
@reboot sleep 30 && sudo /usr/bin/perl /home/pi/notify.pl
The sleep is required to make sure the server has the log file available (didn't work for me without the sleep, I can only assume as the file is deleted on startup):
Reboot your server and you are good to go!
Oct 8, 2017
HOWTO: Setup Minecraft Server on Raspberry Pi 3
Download the Rasbian Lite IMG:
https://www.raspberrypi.org/downloads/
Use Etcher to write the image to your microSD card.
https://etcher.io
Once written boot up Raspbian in your Pi and carry out the following:
Configure your wireless connection if needed:
wpa_passphrase "ESSID" "Password" | sudo tee -a /etc/wpa_supplicant/wpa_supplicant.conf > /dev/null
Where ESSID and Password are wireless network name and connection password respectively.
Upgrade your system:
sudo apt-get update
sudo apt-get upgrade
Install Java:
sudo apt-get install oracle-java8-jdk
Enable SSH via Interface Options
sudo raspi-config
Finish and Reboot
Install Nukkit (the git clone link by default would be https://github.com/Nukkit/, but it didn't support the latest Minecraft version so I found another fork and specific branch)
sudo apt-get install -y git
sudo apt-get install -y maven
git clone -b GT1.2 https://github.com/Creeperface01/Nukkit.git
cd Nukkit
git submodule update --init
mvn clean
mvn package
Now run for the first time and setup the appropriate language:
/usr/bin/java -jar /home/pi/Nukkit/target/nukkit-1.0-SNAPSHOT.jar
Now run the server at boot by adding a command to crontab:
crontab -e
Paste the following into crontab:
@reboot sudo /usr/bin/java -jar /home/pi/Nukkit/target/nukkit-1.0-SNAPSHOT.jar
If you want to access this from anywhere in the world, and not just your local network then your should have your own domain name, then you can forward all connections to your specific machine. Go into your router, forward the specific port (for me it was 19678) to the IP of the machine running Nukkit.
Sep 29, 2017
HOW TO: Install VPN server on Ubuntu when server is behind firewall
The whole point in this post is to run your own VPN service, and allow you to connect remote devices to your home network.
To start off you need to choose a server that is going to be always available, or at least you should try to do that. Next thing is to install OpenVPN on the server and configure it, this can be done in no time at all with the help of the following site:
https://github.com/Nyr/openvpn-install
The first command you are going to need to do is as follows:
wget https://git.io/vpn -O openvpn-install.sh && bash openvpn-install.sh
This downloads and executes the installation script, I had to run this as sudo, so:
sudo wget https://git.io/vpn -O openvpn-install.sh && bash sudo openvpn-install.sh
This script will take you through a variety of questions where you are prompted for entry, in most cases the default option will be appropriate and filled - however if you are running behind a firewall (which you probably will be, I'd like to point out a couple of gotchas).
The IP address of the local machine should indeed be the local IP, there are other sites that suggest this should be the WAN IP of the server, that's fine if the server has direct access to the internet - which mine does not, since it is behind the firewall I choose the local IP so it configures the correct interface to be monitoring.
Next major question is configuring your external IP if you are behind a NAT, honestly you should be using a FQDN and not an IP - check out my previous post on dynu.com options [http://www.geekfreely.com/2015/10/configuring-ddclient-on-ubuntu-server.html]
Once you are finished answering the questions you are ready to make client profiles, run the installer again and you will be prompted a variety of options, you are going to want to add a user:
1) Add a new user
2) Revoke an existing user
3) Remove OpenVPN
4) Exit
Now that you have OpenVPN server installed in Ubuntu, and a client profile created for your device - all you have to do is setup any port forwarding required to the OpenVPN server.
So in my case I setup a rule to forward all 1178 (1194 if you followed the default options) UDP VPN requests from my external IP address to the local IP address of the server running OpenVPN. This was done at my cable modem/router.
That's it, you're done. Let me know if you have any questions or comments below - feel free to donate/tip the creator of the script on the following site:
https://github.com/Nyr/openvpn-install
To start off you need to choose a server that is going to be always available, or at least you should try to do that. Next thing is to install OpenVPN on the server and configure it, this can be done in no time at all with the help of the following site:
https://github.com/Nyr/openvpn-install
The first command you are going to need to do is as follows:
wget https://git.io/vpn -O openvpn-install.sh && bash openvpn-install.sh
This downloads and executes the installation script, I had to run this as sudo, so:
sudo wget https://git.io/vpn -O openvpn-install.sh && bash sudo openvpn-install.sh
This script will take you through a variety of questions where you are prompted for entry, in most cases the default option will be appropriate and filled - however if you are running behind a firewall (which you probably will be, I'd like to point out a couple of gotchas).
The IP address of the local machine should indeed be the local IP, there are other sites that suggest this should be the WAN IP of the server, that's fine if the server has direct access to the internet - which mine does not, since it is behind the firewall I choose the local IP so it configures the correct interface to be monitoring.
Next major question is configuring your external IP if you are behind a NAT, honestly you should be using a FQDN and not an IP - check out my previous post on dynu.com options [http://www.geekfreely.com/2015/10/configuring-ddclient-on-ubuntu-server.html]
Once you are finished answering the questions you are ready to make client profiles, run the installer again and you will be prompted a variety of options, you are going to want to add a user:
1) Add a new user
2) Revoke an existing user
3) Remove OpenVPN
4) Exit
Now that you have OpenVPN server installed in Ubuntu, and a client profile created for your device - all you have to do is setup any port forwarding required to the OpenVPN server.
So in my case I setup a rule to forward all 1178 (1194 if you followed the default options) UDP VPN requests from my external IP address to the local IP address of the server running OpenVPN. This was done at my cable modem/router.
That's it, you're done. Let me know if you have any questions or comments below - feel free to donate/tip the creator of the script on the following site:
https://github.com/Nyr/openvpn-install
Aug 1, 2016
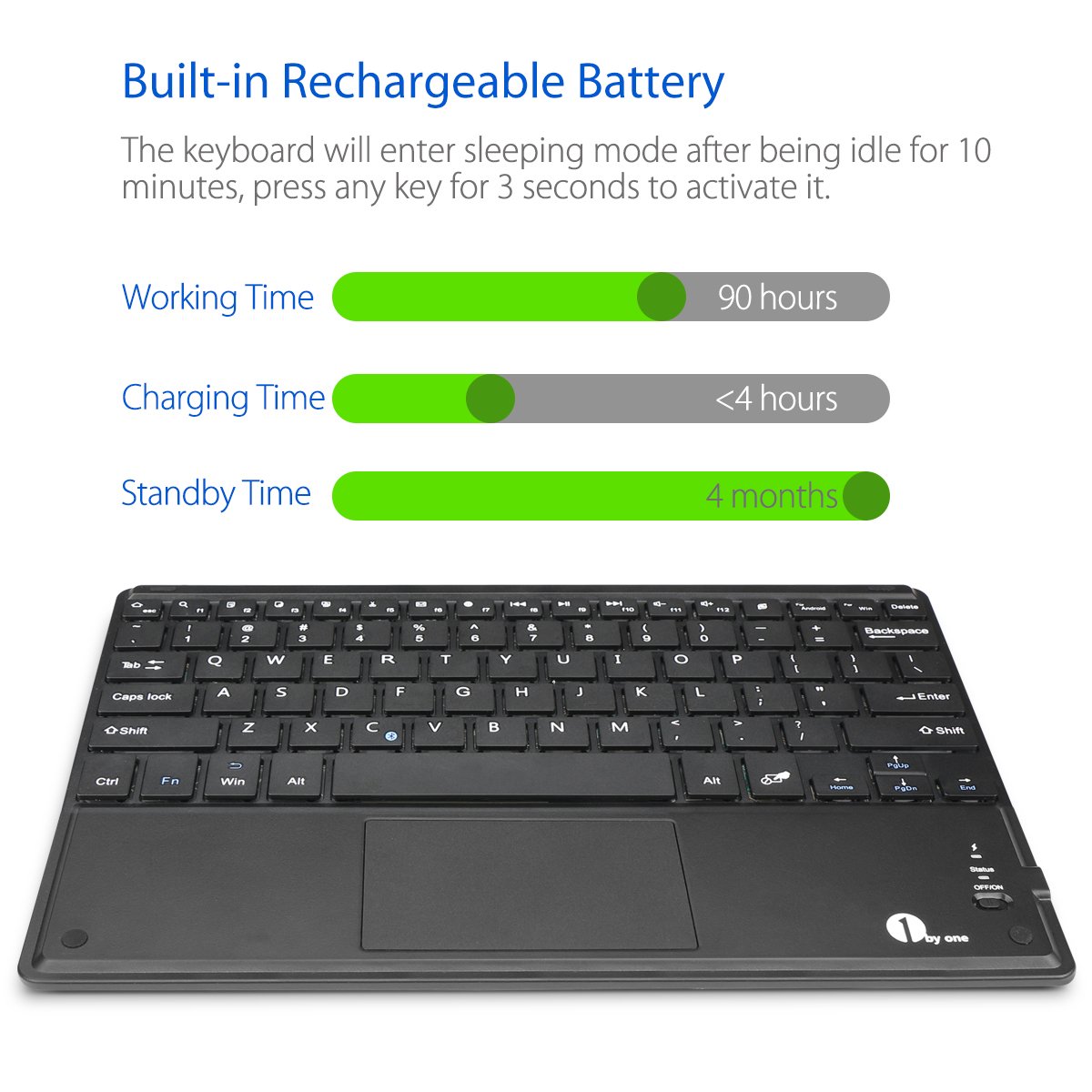
HOW TO: Configure a BlueTooth keyboard for use with Raspbian
I had an old Raspberry Pi 1 lying around and wasn't sure what to do with it - in the end I decided to make myself a thin client for RDP connection to my desktop.
I purchased the following Bluetooth keyboard from Amazon, 1byone Ultra-Slim Wireless Bluetooth Keyboard with Built-in Multi-touch Touchpad and Rechargeable Battery.
First off boot into Raspbian and log in using SSH. Type the following commands:
sudo apt-get install bluetooth bluez blueman
sudo reboot
Once again, log into Raspbian using SSH and type the following:
First off boot into Raspbian and log in using SSH. Type the following commands:
sudo apt-get install bluetooth bluez blueman
sudo reboot
Once again, log into Raspbian using SSH and type the following:
hciconfig
It will shows the Bluetooth device address of the Pi.
Run the following command get the Bluetooth device address of the pair-able devices in range.
hcitool scanto
Then enter the following:
sudo bluetoothctl
agent on
default-agent
scan on
To pair type:
pair xx:xx:xx:xx:xx:xx
Where xx:xx:xx:xx:xx:xx is your Bluetooth device address of the device you want to pair. Next type:
trust xx:xx:xx:xx:xx:xx
connect xx:xx:xx:xx:xx:xx
You should be all good now!
Now I just use remmina to connect to my desktop, and have a nice wireless keyboard to boot!
To pair type:
pair xx:xx:xx:xx:xx:xx
Where xx:xx:xx:xx:xx:xx is your Bluetooth device address of the device you want to pair. Next type:
trust xx:xx:xx:xx:xx:xx
connect xx:xx:xx:xx:xx:xx
You should be all good now!
Now I just use remmina to connect to my desktop, and have a nice wireless keyboard to boot!
Dec 4, 2015
HOWTO: Configuring Kodi to use NAS4Free MySQL DB for central library
If you haven't already installed and setup MySQL on your NAS4Free box, I suggest you follow this guide:
http://www.geekfreely.com/2015/12/howto-mysql-install-guide-for-nas4free.html
We start off by making a for Kodi to access the DB. First we need to login to the MySQL environment to define the user:
mysql -u root -p
Note: If MySQL isn't started then
Enter the password for root and then create the Kodi user, here I call them xbmc for nostalgia:
CREATE USER 'xbmc' IDENTIFIED BY 'xbmc';
GRANT ALL ON *.* TO 'xbmc';
quit;
Create (or add to, if you already have one) an advancedsettings.xml file in your Kodi userdata folder.
Using nano copy and paste the following information into the advancedsettings.xml file, if there is already content, merge the sections appropriately:
advancedsettings.xml configuration found in the following location:
http://kodi.wiki/view/HOW-TO:Share_libraries_using_MySQL/Setting_up_XBMC
And should look like this:
<advancedsettings>
<videodatabase>
<type>mysql</type>
<host>***.***.***.***</host>
<port>3306</port>
<user>xbmc</user>
<pass>xbmc</pass>
</videodatabase>
<musicdatabase>
<type>mysql</type>
<host>***.***.***.***</host>
<port>3306</port>
<user>xbmc</user>
<pass>xbmc</pass>
</musicdatabase>
<videolibrary>
<importwatchedstate>true</importwatchedstate>
</videolibrary>
</advancedsettings>
Replace the two instances of ***.***.***.*** with local network IP address of your NAS4Free server. It is recommended not to use its NetBIOS name, as not all devices may be able to resolve them.
Save the file as advancedsettings.xml. Copy this advancedsettings.xml file you just created to the userdata folder of every Kodi install you want to sync .
If you exported your existing DBs, go ahead and import them. If you created a fresh DB, scan all your content again, make sure to use the NAS4Free server IP rather than NetBIOS for your shares, as mentioned - not all devices may resolve the NetBIOS.
As a final note, specifically with OpenELEC and Raspberry Pi, although OpenELEC suggest this for WiFi boxes, set Wait for network before starting Kodi under OpenELEC addon settings, network.
That is it...you should be good to go. Let me know how it goes for you, or if you have any issues.
http://www.geekfreely.com/2015/12/howto-mysql-install-guide-for-nas4free.html
We start off by making a for Kodi to access the DB. First we need to login to the MySQL environment to define the user:
mysql -u root -p
Note: If MySQL isn't started then
Enter the password for root and then create the Kodi user, here I call them xbmc for nostalgia:
CREATE USER 'xbmc' IDENTIFIED BY 'xbmc';
GRANT ALL ON *.* TO 'xbmc';
quit;
Create (or add to, if you already have one) an advancedsettings.xml file in your Kodi userdata folder.
Using nano copy and paste the following information into the advancedsettings.xml file, if there is already content, merge the sections appropriately:
advancedsettings.xml configuration found in the following location:
http://kodi.wiki/view/HOW-TO:Share_libraries_using_MySQL/Setting_up_XBMC
And should look like this:
<advancedsettings>
<videodatabase>
<type>mysql</type>
<host>***.***.***.***</host>
<port>3306</port>
<user>xbmc</user>
<pass>xbmc</pass>
</videodatabase>
<musicdatabase>
<type>mysql</type>
<host>***.***.***.***</host>
<port>3306</port>
<user>xbmc</user>
<pass>xbmc</pass>
</musicdatabase>
<videolibrary>
<importwatchedstate>true</importwatchedstate>
</videolibrary>
</advancedsettings>
Replace the two instances of ***.***.***.*** with local network IP address of your NAS4Free server. It is recommended not to use its NetBIOS name, as not all devices may be able to resolve them.
Save the file as advancedsettings.xml. Copy this advancedsettings.xml file you just created to the userdata folder of every Kodi install you want to sync .
If you exported your existing DBs, go ahead and import them. If you created a fresh DB, scan all your content again, make sure to use the NAS4Free server IP rather than NetBIOS for your shares, as mentioned - not all devices may resolve the NetBIOS.
As a final note, specifically with OpenELEC and Raspberry Pi, although OpenELEC suggest this for WiFi boxes, set Wait for network before starting Kodi under OpenELEC addon settings, network.
That is it...you should be good to go. Let me know how it goes for you, or if you have any issues.
HOWTO: MySQL install guide for NAS4Free 10.2.x
In some of my previous posts I have written about using NAS4Free and installing various extensions on the system, well it was time to upgrade my NAS4Free but I didn't have the space on the Operating System drive - so a complete re-install was looming.
As daunting as it was, it was inevitable that I had to redo everything, but thanks to the new package manager in FreeBSD 10.x this turned out to be an enjoyable exercise.
The first step I decided to tackle was implementing the MySQL DB on NAS4Free, so I could provide a shared DB for Kodi installs.
First let's determine an appropriate location to install the temporary files for installation:
setenv PKG_TMPDIR /mnt/Data
Next let's create the appropriate user and group for the MySQL install in NAS4Free:
Group
Name: mysql
ID: 88
User
Name: mysql
Fullname: mysql
UserID: 88
Primary Group: mysql
NO PASSWORD
After defining the user to access the MySQL DB, the next step was installing MySQL server, using the following commands:
pkg install mysql56-server
rehash
cd /usr/local
mysql_install_db
At this point it is good practice to confirm that MySQL will indeed starts:
/usr/local/etc/rc.d/mysql-server onestart
Hopefully everything is good at this point and, the next step is to make sure that MySQL is enabled in NAS4Free:
nano /etc/rc.conf
Add the following line to the rc.conf file:
mysql_enable="YES"
Now you should be good to go.
If you want to configure this for Kodi to use, check out the following guide:
http://www.geekfreely.com/2015/12/howto-configuring-kodi-to-use-nas4free.html
As daunting as it was, it was inevitable that I had to redo everything, but thanks to the new package manager in FreeBSD 10.x this turned out to be an enjoyable exercise.
The first step I decided to tackle was implementing the MySQL DB on NAS4Free, so I could provide a shared DB for Kodi installs.
First let's determine an appropriate location to install the temporary files for installation:
setenv PKG_TMPDIR /mnt/Data
Next let's create the appropriate user and group for the MySQL install in NAS4Free:
Group
Name: mysql
ID: 88
User
Name: mysql
Fullname: mysql
UserID: 88
Primary Group: mysql
NO PASSWORD
After defining the user to access the MySQL DB, the next step was installing MySQL server, using the following commands:
pkg install mysql56-server
rehash
cd /usr/local
mysql_install_db
At this point it is good practice to confirm that MySQL will indeed starts:
/usr/local/etc/rc.d/mysql-server onestart
Hopefully everything is good at this point and, the next step is to make sure that MySQL is enabled in NAS4Free:
nano /etc/rc.conf
Add the following line to the rc.conf file:
mysql_enable="YES"
Now you should be good to go.
If you want to configure this for Kodi to use, check out the following guide:
http://www.geekfreely.com/2015/12/howto-configuring-kodi-to-use-nas4free.html
HOWTO: OpenVPN installation guide for NAS4Free 10.2.x
So as you may have read in earlier posts - I did a complete reinstall of my NAS4Free server and setup all services running on it. Here in this post I will describe the steps required to install OpenVPN on your NAS4Free server, and configure it to start automatically on bootup.
First let's determine an appropriate location to install the temporary files for installation:
setenv PKG_TMPDIR /mnt/Data/tmp/
Next let's install all the required components: curl, expect:
pkg install openvpn
pkg install curl
pkg install expect
Typing the following command will update yourr shell session with the new commands available based on the installed packages:
rehash
Move openvpn file so it does not get executed every time thesystem is started, otherwise your boot process will stop and you will be prompted for a username/password. NAS4Free executes all the files inside "rc.d" folder on startup.
mkdir /usr/local/etc/openvpn
mv /usr/local/etc/rc.d/openvpn /usr/local/etc/openvpn/
Edit startup settings and add OpenVPN support:
nano /etc/rc.conf
Add the following:
openvpn_enable=YES"
And ONE of the following, this is based on your VPN provider (check the opvn file contents to determine which to use):
openvpn_if="tun"
openvpn_if="dev"
Now retrieve the relevant information from your VPN provider: certificates, location, configuration files etc. Rename the certificate (*.crt) and chosen location (*ovpn) to openvpn.crt and openvpn.conf, and copy *.pem file.
Install certificates (.crt) and location (.ovpn) files:
mkdir /usr/local/etc/openvpn
mv openvpn* /usr/local/etc/openvpn/
mv *.pem /usr/local/etc/openvpn/
Make sure the certificate authority configuration line (ca) is set to openvpn.crt by editing the following file:
nano /usr/local/etc/openvpn/openvpn.conf
Now it's time to test OpenVPN and make sure you have an appropriate IP.
/usr/local/etc/openvpn/openvpn start /usr/local/etc/openvpn/
curl icanhazip.com
The curl command should return your NAS' new WAN IP, and this should be different to your regular WAN IP - as it should be now based on the location file you provided.
Now we need to configure OpenVP to start and connect on startup, so let's create an auto-sign-on script, and make it executable:
nano /usr/local/etc/openvpn/autosignon
chmod +x autosignon
Paste the following, and edit username and password to match your details, for your VPN provider:
#!/usr/local/bin/expect -f
set force_conservative 0
spawn /usr/local/etc/openvpn/openvpn start /usr/local/etc/openvpn/openvpn.conf
match_max 100000
expect -exact "Enter Auth Username:"
send "YOUR USERNAME"
send "\r"
expect -exact "Enter Auth Password:"
send "YOUR PASSWORD"
send "\r"
expect eof
Add the following command script PreInit (System|Advanced|Command Scripts) via your NAS4Free web interface:
/usr/local/etc/openvpn/autosignon
Reboot your machine and you should be automatically connected to your VPN service.
First let's determine an appropriate location to install the temporary files for installation:
setenv PKG_TMPDIR /mnt/Data/tmp/
Next let's install all the required components: curl, expect:
pkg install openvpn
pkg install curl
pkg install expect
Typing the following command will update yourr shell session with the new commands available based on the installed packages:
rehash
Move openvpn file so it does not get executed every time thesystem is started, otherwise your boot process will stop and you will be prompted for a username/password. NAS4Free executes all the files inside "rc.d" folder on startup.
mkdir /usr/local/etc/openvpn
mv /usr/local/etc/rc.d/openvpn /usr/local/etc/openvpn/
Edit startup settings and add OpenVPN support:
nano /etc/rc.conf
Add the following:
openvpn_enable=YES"
And ONE of the following, this is based on your VPN provider (check the opvn file contents to determine which to use):
openvpn_if="tun"
openvpn_if="dev"
Now retrieve the relevant information from your VPN provider: certificates, location, configuration files etc. Rename the certificate (*.crt) and chosen location (*ovpn) to openvpn.crt and openvpn.conf, and copy *.pem file.
Install certificates (.crt) and location (.ovpn) files:
mkdir /usr/local/etc/openvpn
mv openvpn* /usr/local/etc/openvpn/
mv *.pem /usr/local/etc/openvpn/
Make sure the certificate authority configuration line (ca) is set to openvpn.crt by editing the following file:
nano /usr/local/etc/openvpn/openvpn.conf
Now it's time to test OpenVPN and make sure you have an appropriate IP.
/usr/local/etc/openvpn/openvpn start /usr/local/etc/openvpn/
curl icanhazip.com
The curl command should return your NAS' new WAN IP, and this should be different to your regular WAN IP - as it should be now based on the location file you provided.
Now we need to configure OpenVP to start and connect on startup, so let's create an auto-sign-on script, and make it executable:
nano /usr/local/etc/openvpn/autosignon
chmod +x autosignon
Paste the following, and edit username and password to match your details, for your VPN provider:
#!/usr/local/bin/expect -f
set force_conservative 0
spawn /usr/local/etc/openvpn/openvpn start /usr/local/etc/openvpn/openvpn.conf
match_max 100000
expect -exact "Enter Auth Username:"
send "YOUR USERNAME"
send "\r"
expect -exact "Enter Auth Password:"
send "YOUR PASSWORD"
send "\r"
expect eof
Add the following command script PreInit (System|Advanced|Command Scripts) via your NAS4Free web interface:
/usr/local/etc/openvpn/autosignon
Reboot your machine and you should be automatically connected to your VPN service.
Subscribe to:
Posts (Atom)